Let's Discuss
Enquire NowSafeguard
Machine Learning
Mobile Application
Anomalous Behaviour and Threat Detection in Mobile Web
Rest assured, we have a strict no-spam policy.
Your inbox is safe with us!
Your inbox is safe with us!


4.6
AI Consulting Services and Advanced Data Analytics
5.0
Rated 5-stars by Satisfied customers
BUSINESS REQUIREMENT
The requirement was to make the internet activity secured from threats & unusual behaviour. There should be a proxy based server solution, proxies were used to protect the privacy of the communication that takes place between two users.
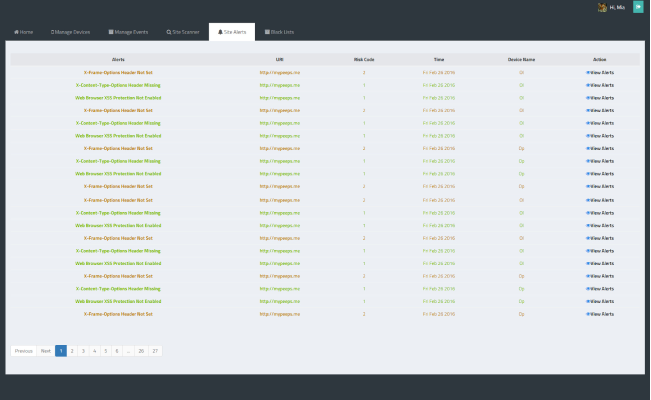
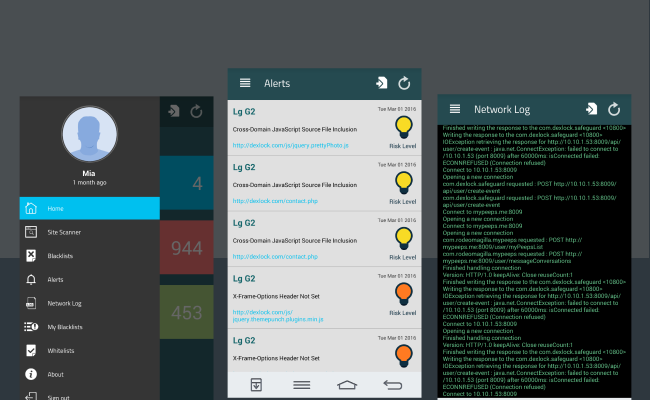
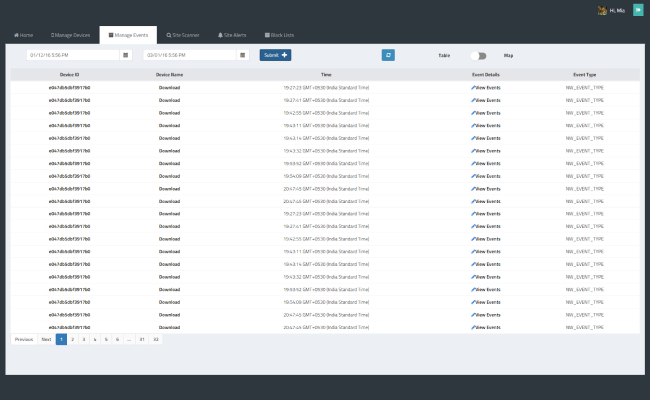
The server was expected to perform actions like penetration testing, site vulnerability analysis, anomaly detection etc. Upon the analysis performed by the server, users were to be notified with the severity of the website status. User gets an option to blacklist or whitelist a particular website, so that they could decide on whether or not to visit the particular website in the future.
CHALLENGES
- Retrieving web traffic from non-rooted phones.
- The time consumed to get the sites scanned and penetration testing was higher.
- The availability of network logs.
- Huge data storage is required, as there are a lot of data to be saved.
SOLUTIONS
- Retrieval of web traffic in a non-rooted phone was tackled by making custom proxy libraries along with credential storage certificates to track proper web traffic results.
- The challenge of time consumption in the penetration technique was reduced by the polling and queuing methods.
- The accuracy of site scanners was made effective by the installation of multiple vulnerability penetration scanners.
- Trained test phase data to identify behaviors of commonly visited websites. The training was then scheduled as a CRON job for the frequent update for the threat signature model.
- Time series databases backed by HBase were used to store huge amounts of data.
IMPACT
- The solution provided a proxy based server, that is now capable of site monitoring and threat notification.
- Universal blacklist is maintained in order to block the sites having malicious content.
- A personalised blacklist can be created by the user, which could further help in parental controls.
KEY TECHNOLOGIES
- Java 8
- OpenTSDB
- ReactJS
- Dropwizard
- Android/iOS
- MongoDB
- HBase
- Deeplearning4J
- OWASP ZAP/ Subgraph Vega