Let's Discuss
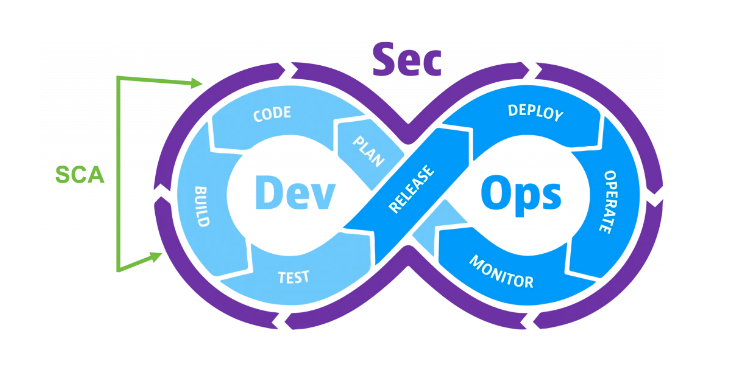
Enquire NowSoftware Composition Analysis (SCA) is a necessity for every company employing open-source software to find security flaws. SCA is an automated method for locating external parts, such as open-source libraries, that are used in programming. Two of the key purposes are to determine whether the program or product we are supplying complies with security and license requirements, as well as to assess the code quality.
Why is this trend gaining traction?
Time to market is one of the primary objectives of any software.
We can start from scratch and write one piece of code for each model and each component to create a business or large-scale software, but this is a slower method. As an alternative, you can use some modules, packages, or models that are currently offered as what is known as FOSS, or free and open-source software, to achieve a quicker time to market. The benefits of using open-source software are that it is something we can immediately use and that there are many minds contributing, which speeds up the process. Nevertheless, utilizing open-source software has unique security difficulties. We cannot just pick a library, include it in our software, and then disseminate it to the whole public with the potential for security flaws.
SCA can help in this situation. It assesses the software’s security so that we can benefit from open-source software and shorten our time to market.
Let us see an example of SCA in action in a real-world setting.
Take a look at WordPress, a well-known content management system (CMS). WordPress has a reputation for adopting antiquated code techniques. There is still a lot of obsolete code and inconsistent development practices. Open-source software benefits from the contributions of many different ideas. But how should we be certain that the donor has addressed every vulnerability? It can just be a cross-site scripting flaw or a password that isn’t encrypted. It may be trivialising the issue, but solving it is a nightmare. One number that comes to mind is that 52% of the 4000 or so vulnerabilities that are known to exist are caused by WordPress plug-ins. These might be plugins for scheduling, payments, etc. And the WordPress core alone is responsible for 37% of the vulnerabilities. Imagine how tight our security must be when the foundation alone has 37% known flaws.
Future of Vulnerability Detection in SCA
The network security portfolio includes SCA in significant amounts. According to our knowledge, an average application’s code is composed of 60–80% Open-Source Software (OSS) components, and according to GitHub, the percentage is around 90% for new applications. The credibility of the software product is at risk due to the increased adoption of OSS components, which opens the door to security flaws. When hackers employ these weaknesses, the firm could suffer significant financial damage.OSS component information is dispersed among thousands of sources. We cannot uncover all vulnerabilities in a single place. Not that all sources are reliable or include an exhaustive list of weaknesses. Although the Common Vulnerabilities and Exposures (CVE) database and the National Vulnerability Database (NVD) attempt to address this issue, not all DB are easily searchable.
Tracking OSS components effectively requires four essential items as part of the SCA process:
- Vulnerability Detection
- Vulnerability Management
- Inventory Management
- OSS License Compliance
One of the first and most important steps in the SCA process is vulnerability detection. We are battling hackers to patch every vulnerability, therefore being able to identify OSS components having known vulnerabilities as soon as feasible is crucial. Zero-day flaws complicate matters due to the limited time to repair them. Attacks that take advantage of these vulnerabilities are on the rise, so if you don’t realize that an OSS component you are utilizing is susceptible, the game is already lost.
Challenges of SCA
All of the software building blocks, or the manifest, of every piece of software that is incorporated into the system, must be always under our watch. It must be a continuous endeavor. Automation can let us regularly check publicly accessible resources like the CVE network or even the national vulnerabilities database in this situation. I advise having things checked as frequently just like every single day. It will be difficult to ask somebody to sit and watch that, of course. Automation undoubtedly facilitates. Resourcing is an obstacle. It is probably necessary to include a specialist on the team.
Depending on the number of the team and the product, SCA may be a separate team that examines all the security flaws or it may be integrated into DevOps. SCA is a component of penetration testing and vulnerability analysis. The most crucial element is that you must prepare for SCA, as well as the size of your group and the product will greatly affect your approach.
Ideas for innovative projects buzzing in your mind? We can be your best development partner. Connect with us here to start something great!
Disclaimer: The opinions expressed in this article are those of the author(s) and do not necessarily reflect the positions of Dexlock.



