Let's Discuss
Enquire NowBusinesses now have serious concerns about cyber security due to the sharp rise in cyber-attacks. Every company, regardless of its size, faces the risk of potential hacker assaults because of the vulnerabilities in their systems, whether it is a startup, SMB, MNC, or the largest organisation in the world. All firms must now have strong cyber security measures if they want to protect themselves from the damages brought on by these dangers. Companies should use security testing to protect their IT infrastructure, networks, apps, and systems against potential threats and weaknesses.
What is Security Testing?
The practice of assessing a system or one or more of its components for security flaws that could be used by malevolent attackers is known as security testing. Assuring the system’s confidentiality, integrity, and availability, as well as confirming that the system secures data and continues to work as intended even when attacked, are the key goals of this kind of testing. Security testing seeks to pinpoint potential security flaws and hazards while also making suggestions for improvement. Penetration testing, vulnerability scanning, network security testing, application security testing, and system security testing are a few examples of the several kinds of security testing.
Why do we need Security testing?
- Finding hidden vulnerabilities: Security testing reveals vulnerabilities or security gaps in the programme or application that, if ignored, could be exploited by hackers.
- Secures sensitive data: By preventing unauthorized access to private data, including credit card numbers, social security numbers, and other personal information, cyber security testing helps to protect consumer and business-sensitive data from all hazards.
-
- Enables regulatory compliance: Organizations must protect consumer data and stop data leaks. This approach enables firms to comply with regulations while assisting with data security.
- Infrastructure protection: Security testing assists companies in protecting their IT infrastructure from malicious attacks and unforeseen hazards.
- Reduces network/app downtime: Cyberattacks may result in the network or app downtime, which can interfere with business operations and the customer experience (CX). Using security testing helps prevent these threats and minimizes or eliminates network or app downtime.
- Savings: Fixing security flaws before deployment is frequently less expensive than resolving them early in the development process. Hence, security vulnerabilities can be discovered early and handled in a way that reduces the overall cost of correcting security issues.
Some cyber threats include:
- SQL Injection
- Malware attacks
- Phishing and Spear Phishing
- Man-in-the-middle attack (MitM)
- Denial of Service attack (DoS)
- Distributed Denial of Service (DDoS)
- Password attack
- Botnet
- IP Spoofing
- Session hijacking
- Ransomware
Some Testing Methods include:
- Static Application Security Testing (SAST):
SAST is a white box security testing method where security flaws are found by inspecting the source code.
- Dynamic Application Security Testing (DAST):
An application is tested while it is running using DAST, a black box testing technique. This aids in discovering security flaws that hackers might use if they went unnoticed.
- Interactive Application Security Testing (IAST):
It entails using software tools to evaluate apps in real time. Using dynamic testing approaches, aids enterprises in identifying and managing security risks and vulnerabilities while running online apps.
- Red Team Assessment:
In order to assess how well an organisation can defend itself against cyberattacks, a team of security professionals, either internal or external, simulates real-time attacks on the business. An organization’s detection and response skills are tested by red team assessments, which also serve to strengthen its security posture.
- Risk-based testing:
It is the process of figuring out and ranking the importance of potential risks related to the programme. The importance and risk of failure are used by the security testing teams to rank the features and functionalities in software.
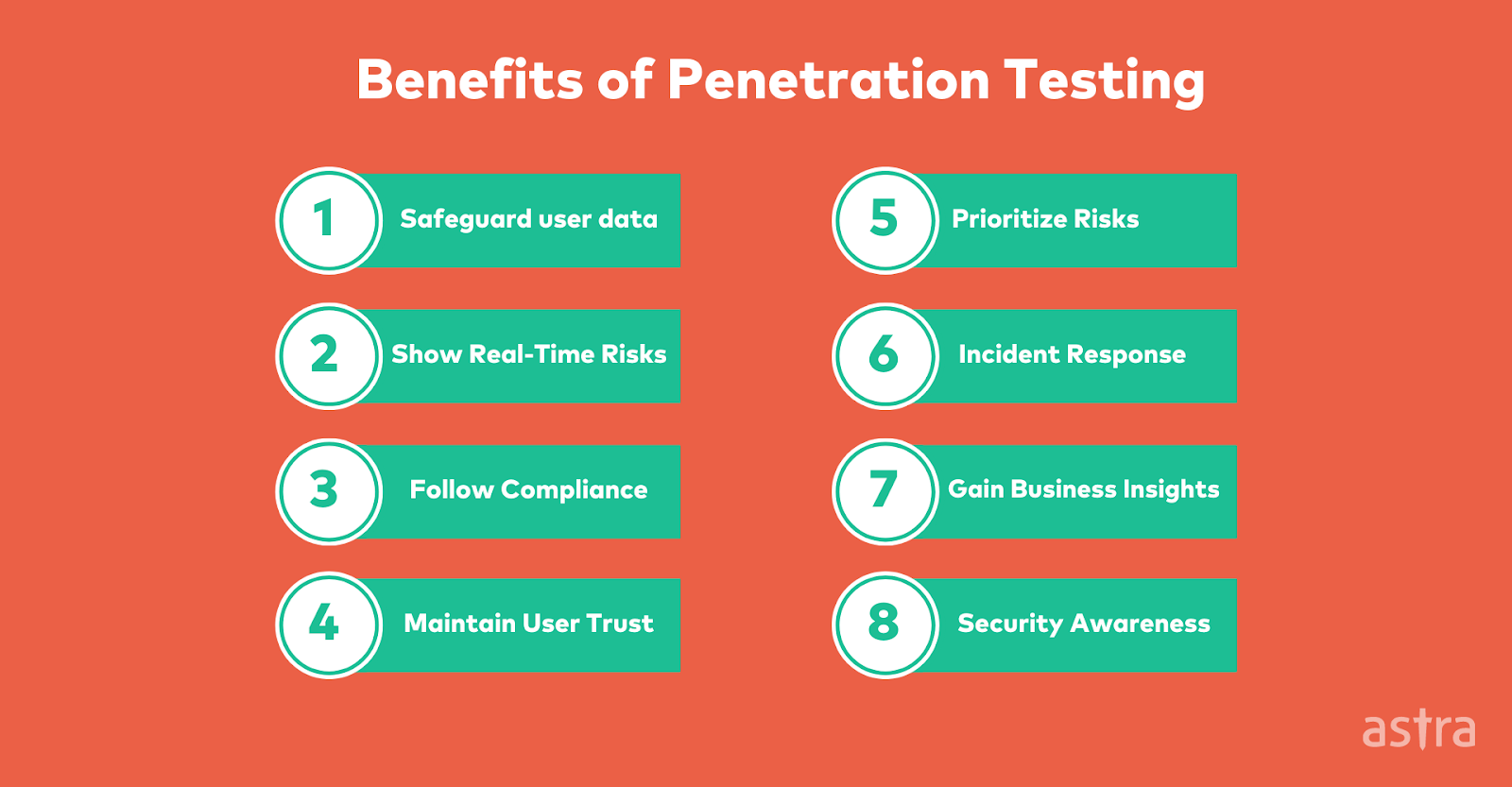
- Penetration testing:
A certified and approved ethical hacker simulates cyberattacks to find software security flaws using the penetration testing approach.
Conclusion
Software must undergo security testing to ensure it is protected against potential cyberattacks. It aids in spotting vulnerabilities, safeguarding private information, preventing unwanted access, ensuring data integrity, and adhering to rules. Businesses may make sure their software is safe and secure from potential threats by doing security testing. Are ideas for innovative projects buzzing in your mind? We can be the best development partner. Connect with us here to start something great!
Disclaimer: The opinions expressed in this article are those of the author(s) and do not necessarily reflect the positions of Dexlock.



